Notifications
Clear all
Topic starter
10/07/2022 3:52 pm
A security analyst has received reports of very slow, intermittent access to a public-facing corporate server.
Suspecting the system may be compromised, the analyst runs the following commands:
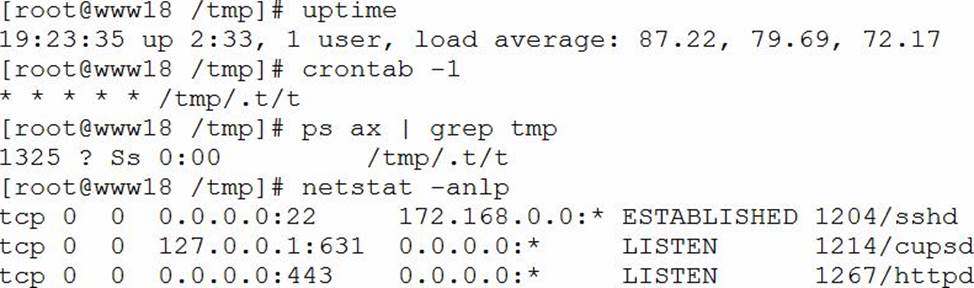
Based on the output from the above commands, which of the following should the analyst do NEXT to further the investigation?
- A . Run crontab -r; rm -rf /tmp/.t to remove and disable the malware on the system.
- B . Examine the server logs for further indicators of compromise of a web application.
- C . Run kill -9 1325 to bring the load average down so the server is usable again.
- D . Perform a binary analysis on the /tmp/.t/t file, as it is likely to be a rogue SSHD server.
Suggested Answer: B
