Notifications
Clear all
Topic starter
When reviewing a compromised authentication server, a security analyst discovers the following hidden file:
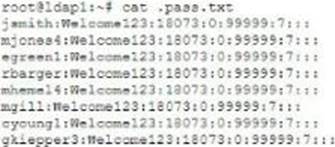
Further analysis shows these users never logged in to the server .
Which of the following types of attacks was used to obtain the file and what should the analyst recommend to prevent this type of attack from reoccurring?
- A . A rogue LDAP server is installed on the system and is connecting passwords. The analyst should recommend wiping and reinstalling the server.
B. A password spraying attack was used to compromise the passwords. The analyst should recommend that all users receive a unique password.
C. A rainbow tables attack was used to compromise the accounts. The analyst should recommend that future password hashes contains a salt.
D. A phishing attack was used to compromise the account. The analyst should recommend users install endpoint protection to disable phishing links.
Suggested Answer: B
Posted : 14/11/2022 6:57 pm
