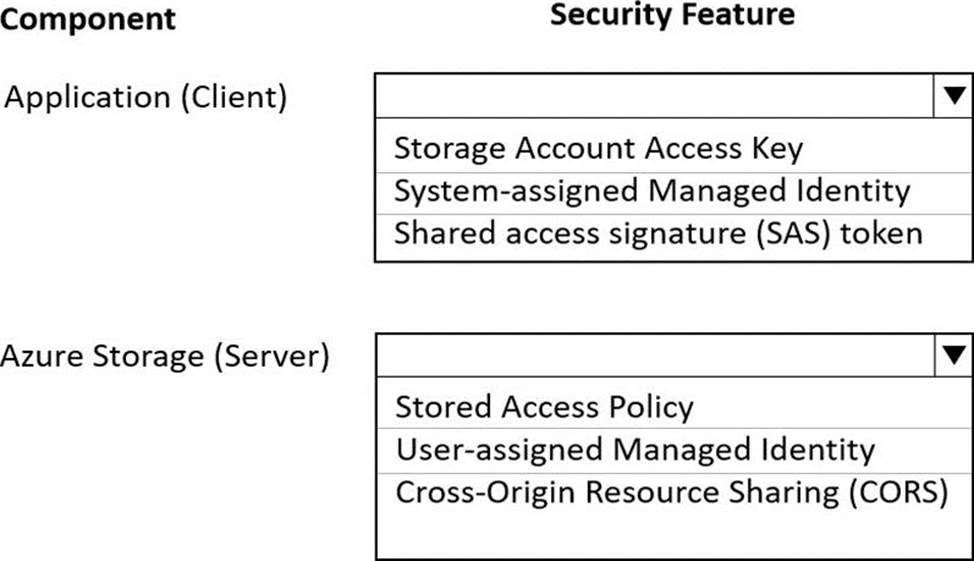
HOTSPOT
You are developing an application to store and retrieve data in Azure Blob storage. The application will be hosted in an on-premises virtual machine (VM). The VM is connected to Azure by using a Site-to-Site VPN gateway connection. The application is secured by using Azure Active Directory (Azure AD) credentials.
The application must be granted access to the Azure Blob storage account with a start time, expiry time, and read permissions. The Azure Blob storage account access must use the Azure AD credentials of the application to secure data access. Data access must be able to be revoked if the client application security is breached.
You need to secure the application access to Azure Blob storage.
Which security features should you use? To answer select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Text, letter
Description automatically generated
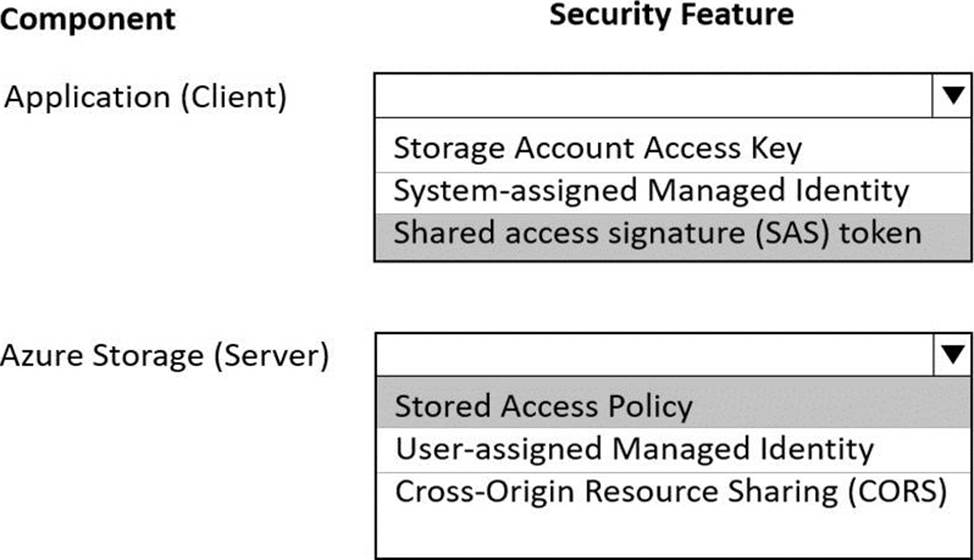
Box 1: Shared access signature (SAS) token
When your application design requires shared access signatures for access to Blob storage, use Azure AD credentials to create a user delegation SAS when possible for superior security.
Box 2: Stored access policy
Stored access policies give you the option to revoke permissions for a service SAS without having to regenerate the storage account keys.
A shared access signature can take one of the following two forms:
✑ Service SAS with stored access policy. A stored access policy is defined on a resource container, which can be a blob container, table, queue, or file share. The stored access policy can be used to manage constraints for one or more service shared access signatures. When you associate a service SAS with a stored access policy, the SAS inherits the constraints C the start time, expiry time, and permissions C defined for the stored access policy.
✑ Ad hoc SAS.
